Cloud security posture management, commonly known as CSPM, is a strategic framework developed to protect cloud environments from security threats. It emphasizes identifying and rectifying misconfigurations and vulnerabilities in cloud platforms, helping businesses stay compliant with security standards and regulations. As organizations increasingly leverage cloud solutions like Google Cloud, AWS, and Microsoft Azure, ensuring a robust and secure cloud stance is crucial. CSPM helps organizations fulfill their part of the shared responsibility model by continuously monitoring their cloud resources, identifying vulnerabilities or misconfigurations, and ensuring that they have implemented appropriate security measures.
As part of SADA’s focus on cloud security, we’re diving into Cloud Security Posture Management, one of the key components of a comprehensive cloud security strategy. In this blog post, you’ll find a list of the three top questions about CSPM, steps to implement CSPM in your organization, and some insights into CSPM best practices.
3 key questions about cloud security posture management
Ready? Let’s dig a bit deeper.
1. What exactly is cloud security posture management (CSPM)?
CSPM is a security tool that enables enterprises to evaluate, oversee, and enhance their cloud security stance. It empowers organizations to pinpoint potential threats, adherence discrepancies, and incorrect setups within their cloud ecosystem.
CSPM solutions use automated tools to analyze cloud environments, detect vulnerabilities, and provide remediation recommendations. CSPM solutions provide visibility into the cloud infrastructure, including access controls, network configurations, data encryption, and other security controls.
Every organization and industry must contend with slightly different cloud security requirements and regulations, but regardless, you will need to protect your cloud environments by understanding their current state and emerging threats.
SADA’s Cloud Security Confidence Program is designed to give you a programmatic approach to cloud security and operations across organizations of all sizes and industries. CSPM is a key component of that programmatic approach.
2. Why is CSPM important?
After completing your cloud migration, it’s crucial to harness the capabilities of automation to keep pace with the evolving threat landscape and safeguard your organization from vulnerabilities.
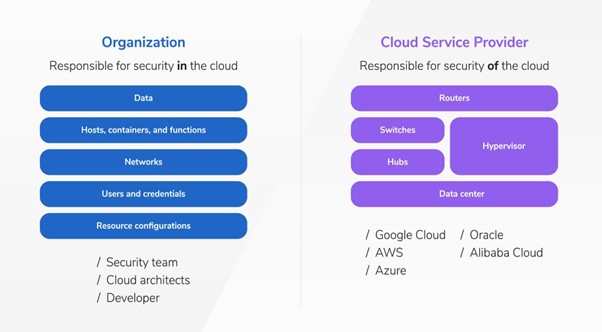
It’s important to remember that cloud security represents a collaborative effort between the cloud provider and the customer. While cloud providers are accountable for fortifying their infrastructure’s security, customers hold the responsibility of safeguarding their data and applications in the cloud.
With the growing adoption of cloud computing, the risks associated with data breaches, compliance breaches, and various security threats are also on the rise. To help organizations identify and remediate security issues before they become exploitable, CSPM gives organizations a comprehensive view of their cloud security posture. In addition, CSPM solutions help organizations maintain compliance with industry regulations, such as GDPR, HIPAA, and PCI DSS.

3. What’s the best way to implement CSPM?
Implementing CSPM requires a holistic approach that covers people, processes, and technology. Your dedicated SADA security team will supply technical and change management expertise, working closely with your internal teams, to implement the CSPM solutions best suited for your unique business.

Here are some common steps to implement CSPM in your organization:
Step 1 – Perform a security assessment
Perform a security assessment to identify security risks, compliance violations, and misconfigurations in your cloud environment. SADA offers a Cloud Security Confidence Assessment that evaluates current controls and provides recommendations and best practices to help reduce risks and prepare for threats.
Step 2 – Define security policies
Define your security policies for the cloud environment, including access controls, data encryption, network segmentation, and other security controls.
Step 3 – Devise a CSPM solution
Devise a CSPM solution that meets your organization’s security requirements. CSPM solutions are available as SaaS, on-premises, multi-cloud, or hybrid deployments.
Step 4 – Integrate CSPM solution
Integrate your CSPM solution with your cloud environment. This involves configuring the solution to access your cloud environment, including providing credentials and permissions.
Step 5 – Remediate security issues
Remediate security issues identified in the security assessment. CSPM solutions provide remediation recommendations, but you may need to modify your security policies or cloud configurations to address any issues.
Step 6 – Continuous monitoring
Continuous monitoring is essential to maintain your security posture in the cloud. CSPM solutions provide real-time visibility into your cloud environment, allowing you to detect and remediate security issues as they occur.

3 benefits of cloud security posture management
1. CSPM provides visibility
Cloud security posture management (CSPM) stands as an invaluable tool that equips organizations with a holistic perspective of their cloud environment. It encompasses all facets, spanning from infrastructure and applications to the array of services employed within the cloud. This depth of visibility grants organizations a profound understanding of their cloud configuration and ongoing operations. Armed with this insight, security teams are well-equipped to vigilantly oversee and govern the security of their cloud assets. By maintaining a clear and real-time depiction of their cloud landscape, organizations can proactively spot potential vulnerabilities and security gaps, enabling them to swiftly bolster their security posture and safeguard their digital assets. In essence, the visibility that comes along with CSPM empowers organizations to make informed decisions and uphold robust security within the dynamic realm of cloud computing.
2. CSPM helps you detect and respond to misconfigurations
Cloud security posture management (CSPM) tools excel at the crucial task of detecting misconfigurations within your cloud resources and security settings. These misconfigurations, if left unattended, can pose significant security risks. CSPM goes beyond just identifying these issues; it takes swift action. When CSPM detects misconfigurations, it doesn’t stop at identification. Instead, it immediately triggers alerts and offers clear guidance on how to correct these problems. This proactive approach substantially reduces security risks by ensuring that vulnerabilities are promptly addressed, enabling organizations to maintain a resilient and secure cloud infrastructure. CSPM acts as a vigilant guardian against the potentially severe consequences of misconfigurations in the ever-evolving cloud landscape.
3. CSPM helps you maintain compliance
Cloud security posture management (CSPM) serves as a vital guardian for organizations aiming to maintain compliance within their cloud infrastructure. By continuously monitoring and assessing the cloud environment, CSPM ensures that industry regulations and internal policies are rigorously upheld. It meticulously verifies adherence to key standards such as GDPR, HIPAA, and any specific requirements relevant to the organization’s industry. CSPM not only aids in preventing potential legal and regulatory issues but also provides assurance that the highest levels of data security and privacy are maintained. In essence, CSPM proactively enforces compliance, mitigating compliance-related risks.

Differences between CSPM and other cloud security solutions
Cloud security posture management (CSPM) and other cloud security solutions have specific roles in safeguarding cloud environments. Here’s a simplified breakdown of the distinctions between CSPM and three other cloud security solutions: cloud infrastructure security posture assessment (CISPA), cloud workload protection platforms (CWPPs), and cloud access security brokers (CASBs):
CSPM (cloud security posture management)
Focus: CSPM primarily centers on assessing and guaranteeing the security of your cloud infrastructure’s setup and preferences.
Purpose: It leverages automation to aid in detecting misconfigurations, ensuring alignment with security regulations, and identifying security weaknesses in your cloud assets like databases, storage, and virtual networks.
Example: CSPM tools can detect issues like exposed ports, insecure storage buckets, or improperly configured firewalls in your cloud setup.
CISPA (cloud infrastructure security posture assessment)
Focus: CISPA, a first-generation CSPM, centers on assessing the security of your cloud infrastructure.
Purpose: It provides a snapshot of your cloud environment’s security posture by evaluating factors like network configurations, access controls, and adherence to security best practices. It mainly focuses on reporting.
Example: CISPA tools can alert you if sensitive data is accessible to the public, helping you maintain a secure infrastructure.
CWPP (cloud workload protection platforms)
Focus: CWPPs shift their attention from infrastructure to the security of workloads, including applications, containers, and virtual machines.
Purpose: These platforms secure the runtime environment of your workloads by offering protection against malware, intrusion attempts, and vulnerabilities specific to applications and processes.
Example: A CWPP might identify and block suspicious activities within a cloud-based application, preventing data breaches or disruptions.
CASB (cloud access security brokers)
Focus: CASBs are primarily concerned with controlling and enhancing the security of access to cloud applications and data, especially when accessed from various devices and locations.
Purpose: They act as intermediaries, enforcing security policies, granting visibility into user activities, ensuring compliance with regulations, and preventing data leaks.
Example: CASBs can limit access to sensitive files based on user permissions, encrypt data before it’s uploaded to the cloud, and monitor user actions for unusual patterns.

Best programs and practices for managing cloud security
With the increasing adoption of hybrid and multi-cloud environments, organizations are wise to use a management platform to ensure that their cloud security posture remains consistent across all environments and at scale. Combining a CSPM with SADA’s Cloud Security Confidence Program establishes a well-rounded strategy for defending your assets.
“It’s important to us at SADA that we maintain a view of the entire security and regulatory landscape, across every possible industry and enterprise,” says Rocky Giglio, SADA’s Director, Security Go-to-Market & Solutions. “And while SADA’s security experts have developed best practices drawn from industries that handle the most sensitive data, including healthcare, finance, and government, the threat landscape is ever evolving and environments change constantly. Having a CSPM in place along with the practices built into SADA’s Cloud Security Confidence Program provides you the confidence to confront evolving cyber threats.”
SADA helps businesses across the globe implement tools designed to secure cloud environments. Your dedicated SADA security team will help you navigate complex cyber landscapes, ensuring that your cloud security posture remains compliant with industry and government regulations. In addition, SADA’s Flex Services team provides ongoing monitoring and management of your cloud security posture, freeing your in-house resources to focus on core business activities.
For an even deeper dive into the latest insights on cloud security, register to watch SADA Ground School on demand, the cloud transformation summit with a full slate of programming related to cyber threats and how to confront them. And be sure to catch the session, “What does cloud security posture management mean for your organization?”

FAQ
CSPM stands for “Cloud Security Posture Management.” It’s a cybersecurity approach and a set of tools that focus on assessing and improving the security of your cloud infrastructure and configurations.
CSPM benefits include enhanced security, compliance assurance, real-time monitoring, cost savings, improved visibility, automation, risk reduction, scalability, centralized management, and continuous improvement.
CASB (Cloud Access Security Broker) focuses on securing data and access to cloud services, while CSPM (Cloud Security Posture Management) focuses on securing the configuration and compliance of the cloud infrastructure itself. CASB is about data protection and access control, while CSPM is about infrastructure security and compliance checks. Both are crucial for comprehensive cloud security.



