Enterprise cloud security

In the fast-paced digital era, businesses are progressively turning to cloud computing to enhance efficiency, cut down costs, and scale with ease. As organizations transfer their vital data and apps to the cloud, prioritizing stringent security becomes paramount. Let’s take a deep-dive into enterprise cloud security and examine its relevance, associated risks, and common obstacles. We’ll also explore essential tactics to shield invaluable cloud assets.
What is enterprise cloud security?

Enterprise cloud security encompasses the holistic strategies, tools, and procedures implemented to safeguard an organization's data, applications, and infrastructure within cloud platforms. This protective approach spans across different cloud models such as public, private, and hybrid, ensuring the integrity and safety of services and data housed in these setups.
Why enterprise cloud security is important
A comprehensive enterprise cloud security strategy is vital, especially considering the pivotal role cloud services hold in today's business dynamics. Here's why it's essential:
1. Data protection
The cloud stores a plethora of sensitive information, ranging from client details to proprietary knowledge. Robust security protocols are crucial to avoid unauthorized access and data exposure. In addition to securing data at rest, it is crucial to encrypt data during its transmission to uphold its confidentiality. Strong encryption protocols and key management practices are imprtant components of data protection in the cloud.
2. Business continuity
Downtime or data loss can have severe consequences. Robust cloud security ensures business continuity and minimizes disruptions. Cloud disaster recovery plans and backup strategies are integral in case of unforeseen incidents.

3. Regulatory compliance
Many industries have strict regulatory requirements regarding data security and privacy. Non-compliance can result in hefty fines and damage to an organization's reputation.
Enterprises must stay informed about relevant regulations and ensure that their cloud security measures align with these standards. Regular audits and compliance checks are essential.
4. Reputation management
A security lapse can damage a company's reputation and diminish client confidence. Guarding against such events is essential to uphold a favorable brand image. Demonstrating a commitment to security can build trust.
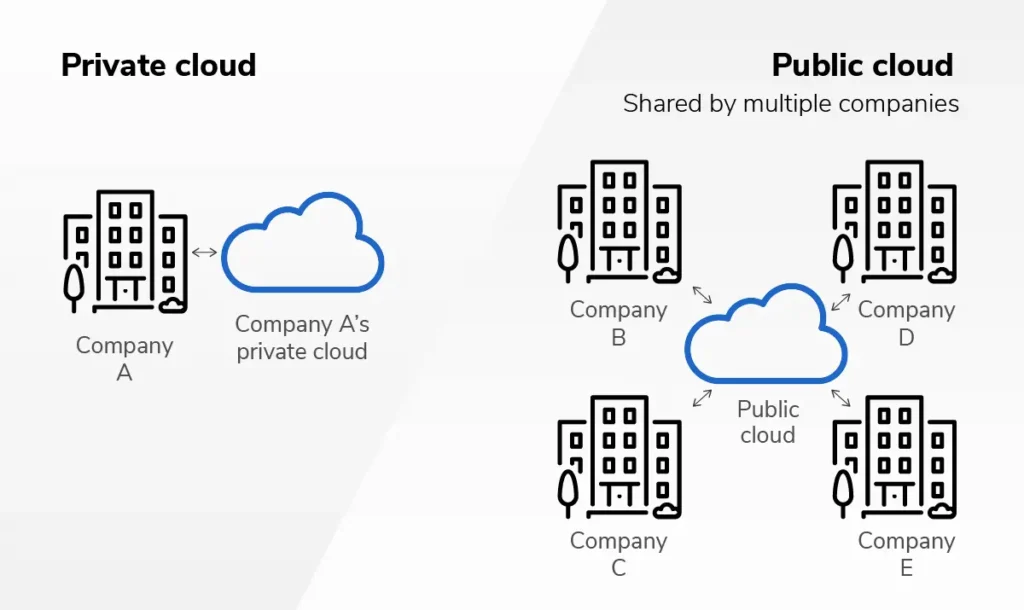
How secure are public vs. private clouds?
Public and private clouds offer different security challenges and advantages:
Public clouds
In shared public cloud environments, the responsibility for security is typically divided between the cloud provider and the customer. While leading providers invest heavily in security measures, customers must also secure their data and applications through proper configuration and access controls.
Implementing robust access controls, encryption, and regular security assessments are essential in public cloud environments. Cloud providers often offer a wide range of security tools and services that organizations can leverage.
Private clouds
Private clouds offer more control and customization but require organizations to shoulder a higher security burden. They are well-suited for highly regulated industries or organizations with particularly sensitive data.
In a private cloud, organizations have greater control over security configurations. However, this control also means they must stay vigilant in monitoring and maintaining security measures.
What are threats to enterprise cloud security?

There are a number of threats to enterprise cloud security that you need to be aware of. Here are some of the most prominent:
Misconfiguration
Misconfigured cloud assets often pose significant security threats. Such oversights can lead to exposed confidential data or allow unwarranted access. To counter these risks, companies should adopt infrastructure-as-code (IaC) methodologies, carry out consistent security assessments, and educate their IT teams tasked with setting up cloud assets.
Denial-of-Service (DoS) attacks
To mitigate DoS attacks, where adversaries inundate cloud services with excessive traffic, causing disruptions and rendering resources inaccessible, organizations can implement defensive measures such as traffic filtering, rate limiting, and leveraging content delivery networks (CDNs) to absorb sudden traffic surges. Additionally, monitoring for atypical traffic patterns remains crucial.
Cyberattacks
Malware, ransomware, and other cyber threats can compromise cloud environments, leading to data breaches or service disruptions.
Robust endpoint security, email filtering, and network intrusion detection systems can help detect and prevent cyberattacks. Regular software patching and updates are crucial to addressing known vulnerabilities.
Unprotected APIs
Inadequately secured Application Programming Interfaces (APIs) can provide attackers with a gateway to sensitive data.
Security practices such as API authentication, authorization, and thorough testing are vital to protect against API-related threats. Organizations should also monitor API usage for suspicious activity.
Account takeover
Unauthorized access to user accounts can lead to data theft, unauthorized transactions, or service abuse.
Implementing strong multi-factor authentication (MFA) and continuously monitoring user account activity for unusual behavior can help prevent account takeovers.
Data leaks
Sensitive data can be exposed through various means, including misconfigurations, insider threats, or external attacks.
DLP tools, encryption methods, and user awareness are essential in thwarting data leaks. Access to confidential information should be limited, granted only when absolutely necessary.
What are the challenges of enterprise cloud security?
Securing the cloud poses unique challenges:
Multitenant cloud environments
In public clouds, multiple tenants share the same infrastructure. Isolating resources and data from other tenants is essential.
Network segmentation, access controls, and encryption are key strategies that SADA can help you with to ensure the security and privacy of data in multitenant environments. Additionally, our experts can help you fully leverage tools that cloud providers offer for resource isolation and tenant-specific security configurations.

Lack of visibility
Enterprises often lack full visibility into their cloud environments, making it challenging to monitor and secure all assets effectively.
SADA can help your organization gain insight into your cloud deployments by empowering you with cloud security tools that provide comprehensive visibility, such as cloud security posture management (CSPM) and cloud workload protection platforms (CWPP).
Shadow IT
Employees may use unauthorized cloud services (shadow IT), bypassing corporate security measures and increasing the attack surface.
Encouraging employees to work within approved cloud services and providing user-friendly alternatives can help reduce the prevalence of shadow IT. Additionally, organizations can implement cloud access controls to monitor and control unsanctioned cloud usage.
Dynamic workloads
Cloud environments are highly dynamic, with workloads constantly shifting. Traditional security measures may struggle to keep up.
SADA security experts can help you implement automated security policies that adapt to the dynamic nature of cloud workloads. Infrastructure as code (IaC) practices can help automate security configurations, ensuring consistency and agility.
Regulatory compliance
Meeting compliance requirements across different regions and industries can be complex and demanding.
It's crucial for organizations to possess a comprehensive understanding of the regulatory landscape pertinent to their industry and geographical scope. SADA provides tailored compliance frameworks and cloud security services, specifically designed to facilitate and streamline the compliance process.
What are the keys to enterprise cloud security?

To strengthen cloud security, organizations should implement a multi-layered approach:
Identity and access management
Strict control over user access, strong authentication, and identity verification are crucial components of cloud security.
Implementing identity and access management (IAM) policies, role-based access control (RBAC), and regular access reviews are fundamental practices. Additionally, adopting single sign-on (SSO) and privileged access management (PAM) solutions can enhance security.
Continuous monitoring
Real-time monitoring of cloud environments helps you detect and respond to threats promptly.
Leveraging security information and event management (SIEM) systems, intrusion detection systems (IDS), and security automation can provide real-time insights and automated response capabilities.
Cloud network security
Protecting cloud networks through firewalls, intrusion detection, and encryption is essential.
Utilizing cloud-native security services and configuring network security groups (NSGs) or security groups (SGs) can help secure cloud networks. Implementing micro-segmentation can further enhance network security by isolating workloads.
Data protection
Implementing encryption, data masking, and backup strategies safeguards sensitive information.
Encryption should be applied to data at rest, data in transit, and data in use. Organizations should also regularly back up data and test data recovery procedures to ensure data integrity and availability.
Threat intelligence
Staying informed about emerging threats and vulnerabilities is essential to proactively address potential risks.
Subscribing to threat intelligence feeds, participating in industry information-sharing groups, and conducting threat hunting activities can help organizations stay ahead of evolving threats.
Cloud access security brokers (CASBs)
CASBs provide a layer of security between users and cloud services, helping to enforce security policies and detect anomalies.
Implementing CASBs can provide granular control over cloud access, data protection, and threat detection. These solutions enable organizations to extend their security policies into cloud environments.
Zero trust network access (ZTNA)
ZTNA assumes that no user or device should be trusted by default and requires authentication and authorization for every access request.
Adopting a zero trust architecture involves verifying and securing access at every step of the user's journey, from authentication to resource access. This approach helps prevent unauthorized access and lateral movement within cloud environments.
Prepare and fortify your organization against any threat with SADA
Enterprise cloud security is a critical aspect of modern business operations. With the ever-evolving threat landscape, organizations must adopt a proactive and multi-faceted approach to protect their cloud resources effectively. SADA’s security experts can help you understand the challenges and implement robust security measures, enabling you to confidently harness the power of the cloud while keeping your digital fortress secure. Remember that cloud security is an ongoing process that requires continuous assessment, adaptation, and improvement to stay ahead of emerging threats. Boost your confidence in your security posture by signing up for a Cloud Security Confidence Assessment.

FAQ
Enterprise cloud security refers to the comprehensive strategies, tools, and protocols put in place to safeguard an organization's data, applications, and infrastructure within cloud environments. This includes ensuring the confidentiality, integrity, and availability of data across various cloud models such as public, private, and hybrid.
LET'S TALK
Our expert teams of consultants, architects, and solutions engineers are ready to help with your bold ambitions, provide you with more information on our services, and answer your technical questions. Contact us today to get started.